With the average cost of a single data breach estimated at $4.45 Million USD (IBM, 2023) and a global aggregated cost of $8 Trillion USD per year (Cybersecurity Ventures), cybersecurity is a hot topic. From small businesses to critical infrastructures, everyone is currently at risk of a cyber attack.
Cybersecurity is the practice of protecting internet-connected devices, services and its users from malicious attacks. Common attacks include phishing schemes, ransomware attacks, identity theft, data breaches, and financial losses. Cybersecurity involves processes, technologies and tools designed to enhance user, application, and network security.
With commercial organizations becoming in-space users and service providers, there is growing concern about cybersecurity in the space domain. For instance, the NIST National Cybersecurity Center of Excellence has issued guidelines for hybrid satellite networks and other documentation addressing the cybersecurity aspects of satellite networks.
In interplanetary networks, existing security frameworks, architecture and protocols used in the terrestrial internet face challenges due to long delays, disruptions, and other link and hardware characteristics which challenge key assumptions used in terrestrial internet security. For example, the long delays and disruptions may compromise the continuous access to Public or Private Key Infrastructure used for validation of keys. Also, conversational security protocols such as IKEv2 (Internet Key Exchange) may not be usable because the time required to complete the messaging to do key exchange may take an unreasonable amount of time at interplanetary distances.
Research and development for security of interplanetary networks have focused primarily on network security as a foundational capability. As the Bundle Protocol is the internetworking layer for interplanetary networks, network security has been based in securing the Bundle Protocol.
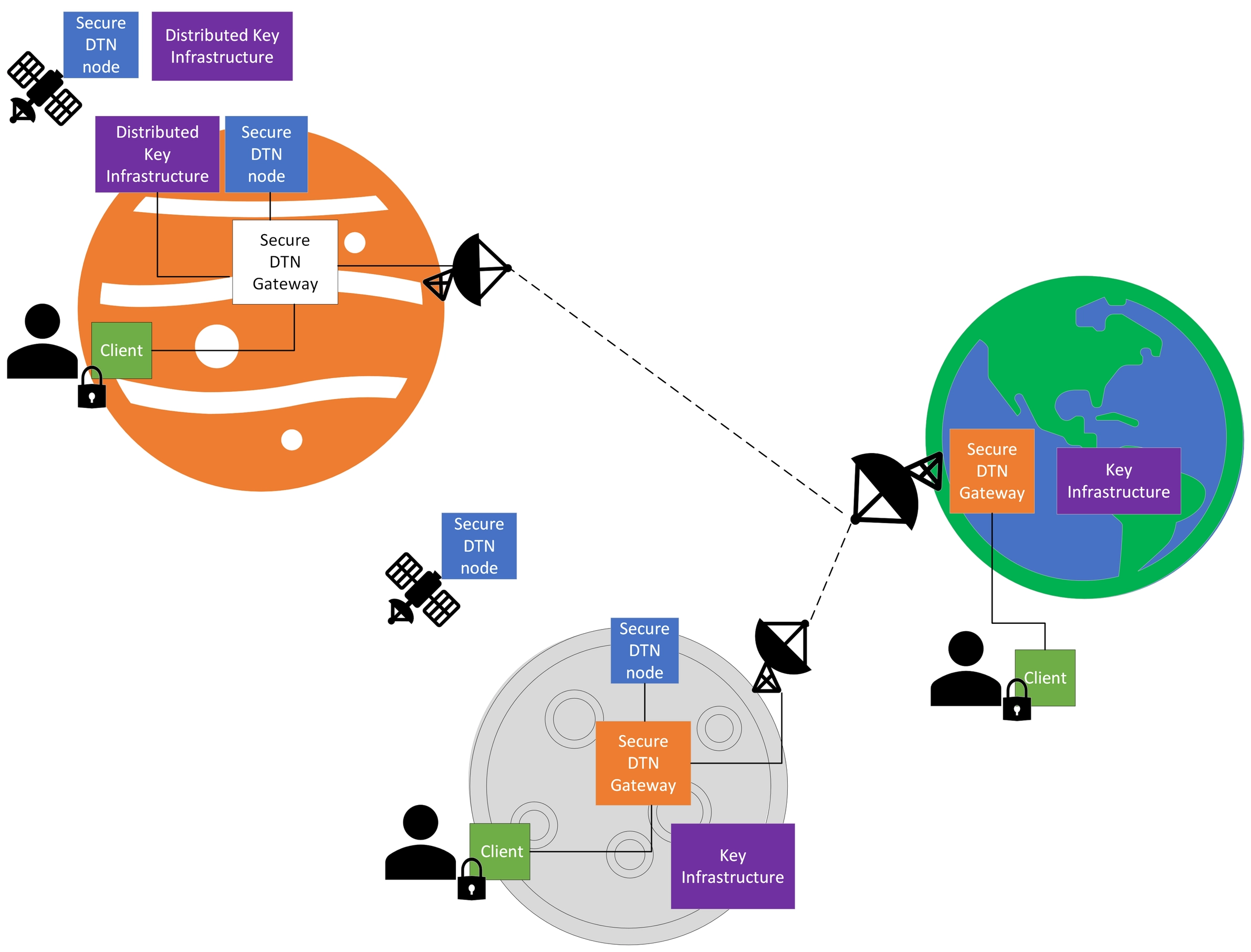
Conceptual view of a secure interplanetary DTN network.
Bundle Protocol Security (BPSec)
The Bundle Protocol Security (BPSec) is formally specified in the IETF RFC 9172 technical specification. It defines security bundle extension blocks to apply security services to the contents of a bundle.
The primary goal of BPSec is to provide Confidentiality and Integrity services. As such, there are two types of security blocks defined: the Block Integrity Block (BIB) and the Block Confidentiality Block (BCB).
- Block Integrity Block (BIB). Ensures integrity by holding key information and digital signatures for each of its security target(s). This integrity information may be verified by any node in between the BIB security source and the bundle destination. Security-aware waypoints may add or remove BIBs from bundles in accordance with their security policy.
- Block Confidentiality Block (BCB). Protects the content while in transit by encrypting the contents of its security target(s), in whole or in part, at the security source. The BCB may be decrypted by security-aware nodes in the network, up to and including the bundle destination, as a matter of security policy.
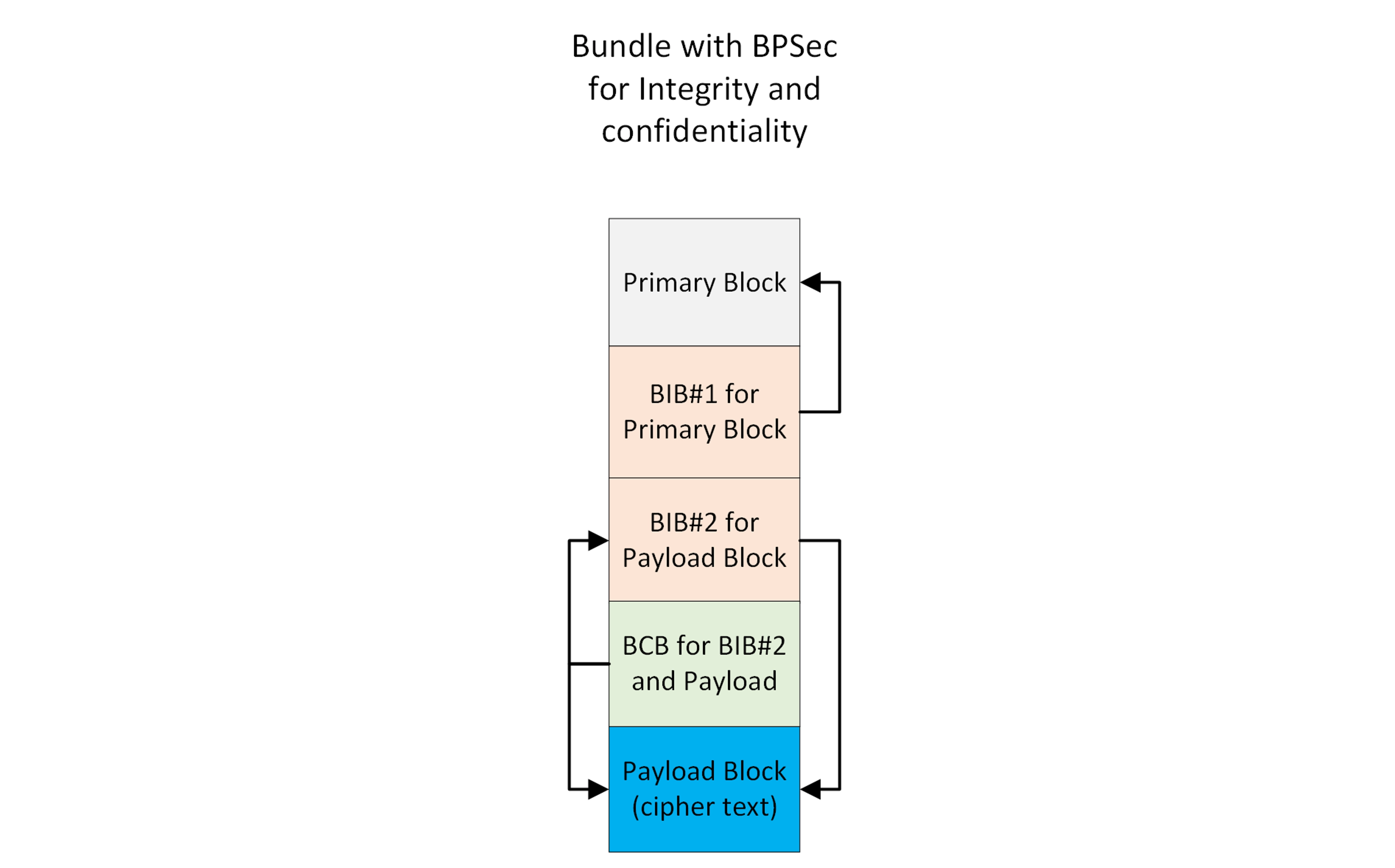
Example bundle with primary block integrity protected, and payload block with integrity and confidentiality protection.
Specific rules have been established to ensure consistency and flexibility of operations in the use of security blocks for integrity and confidentiality security services. The specification provides rationale as of why these rules are set.
- Disallowed to encrypt the payload twice.
- Allowed to integrity sign different blocks.
- Allowed to sign and encrypt the same block.
- In cases where the same security service (with same key, cipher suite) is applied to multiple blocks by the same security source, it is possible to represent this operation by a single security block. This is to optimize the resulting bundle size by avoiding repetition.
- Integrity services must always be applied before confidentiality services. Therefore, a Block Integrity Block (BIB) cannot target a Block Confidentiality Block (BCB) under any circumstance.
- If confidentiality is being applied to a target block that also contains integrity services, then the confidentiality must also protect the integrity service.
- The confidentiality service must be handled first to decrypt the blocks representing the integrity service, then the integrity service can be handled.
Bundle Security Blocks specify the use of Security Contexts. They are a set of configurations, algorithms and policies used in the implementation of the security services that can be applied consistently by nodes in the network. There are a set of default Security Contexts defined in the IETF 9173 technical specification.
It is important to note that the BPSec specification assumes that key management is handled as a separate part of network management, therefore it does not define or require a specific strategy for key management.
For those interested in learning more about BPSec, Securing Delay-Tolerant Networks with BPSec provides an in-depth review of this protocol and DTN security in general.
Open topics
There are a myriad of open topics in the security of DTN networks. The list below, although not exhaustive, represents some of the key open topics in the area of security for interplanetary networks.
- Delay Tolerant Key Management: At interplanetary distances, communications are realized over frequent disruptions and extensive delays, therefore security keys may not be properly negotiated (the communication opportunity might be too short), and/or public keys and certificates can't be obtained by query (the communication opportunity may not be available to obtain the key). S. Burleigh et al at the Jet Propulsion Laboratory proposed DTKA - a Delay-Tolerant Key Administration, depicting a way to perform Key Distribution that overcomes the delay and disruption challenges of Interplanetary communications. A prototype implementation was created, although no additional progress have been made for its specification.
- Protections against topology attacks: Current Bundle Protocol network topology is flat. In this architecture, all nodes have universal routing information. For example, an attacker that is able to compromise a node may be able to obtain routing information for the entire network, with the ability then to perform near or on-path attacks to virtually the entire network. S. Burleigh also proposed Bundle-in-Bundle Encapsulation (BIBE), a bundle encapsulation mechanism whereby a bundle may be made the payload of a second bundle. This allows for topology hiding and the implementation of more complex security combinations. Although its specification has not yet progressed to become a technical specification, there are some implementations available.
- Zero Trust architecture for interplanetary networks: There is growing evidence that castle-and-moat (i.e. network perimeter) based security is not enough to protect a network, its applications and users, therefore more comprehensive frameworks and architectures have emerged. Zero Trust (never trust, always verify) is a dominant architecture for securing internet services, offering user, application and network security services. We evaluated the considerations for extending the Zero Trust Architecture to DTN networks in space, uncovering gaps such as the need to adapt identity and access services, content inspection and node compromise protections to the characteristics of interplanetary communications. These considerations were presented at the 2023 IEEE/NASA Cognitive Communications for Aerospace Applications (CCAA) workshop.
This article was shared via The Bundle, Spatiam's quarterly newsletter.
Header image: Property of NASA.
